Cybercriminal groups, primarily based in China, are shifting their SMS phishing tactics. Previously known for scams involving fake package deliveries or unpaid toll fees, these groups are now deploying new schemes, particularly as the holiday shopping season approaches. They are offering phishing kits that enable the creation of realistic-looking e-commerce websites designed to steal payment card information and link it to mobile wallets like Apple Pay and Google Pay. Additionally, these groups are using SMS messages to lure individuals with promises of unclaimed tax refunds and mobile rewards points.
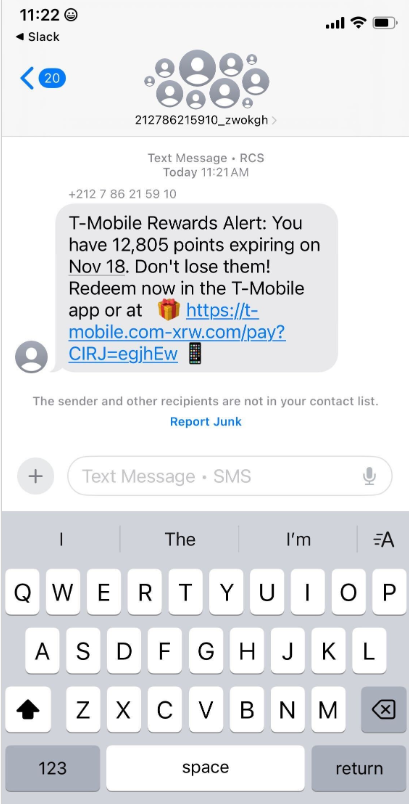
Recently, numerous domain names have been registered for fraudulent websites targeting T-Mobile customers. These sites falsely claim to offer a significant amount of rewards points. The scam messages promoting these domains are distributed through Apple’s iMessage and Google’s RCS messaging services.
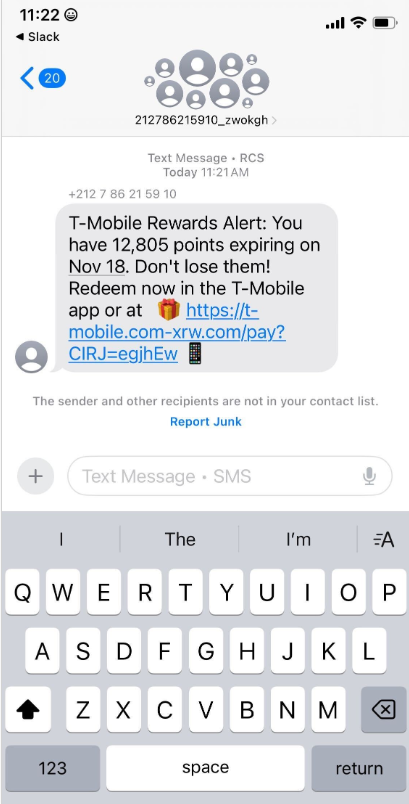
An instant message impersonating T-Mobile, claiming eligibility for thousands of rewards points.
According to the website scanning service urlscan.io, thousands of these phishing domains have been activated in a short period. These fraudulent websites are designed to load only when accessed from a mobile device. They prompt visitors to enter personal details, including name, address, phone number, and payment card information, under the guise of claiming rewards points.
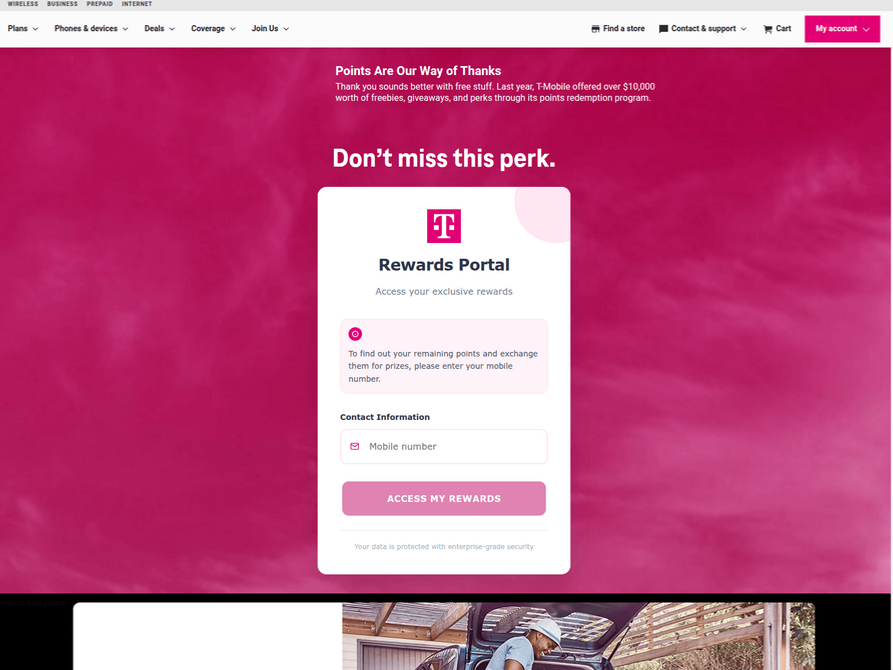
A recently registered phishing website designed to mimic T-Mobile.
Upon submitting card data, users are then asked for a one-time code sent via SMS by their bank. This code is actually generated because the fraudsters are attempting to enroll the stolen card details into a mobile wallet like Apple Pay or Google Pay. If the victim provides this one-time code, the phishers can successfully link the victim’s card to a mobile device they control.
Further investigation using urlscan.io, starting from the T-Mobile phishing domains, uncovered a similar scam aimed at AT&T customers:
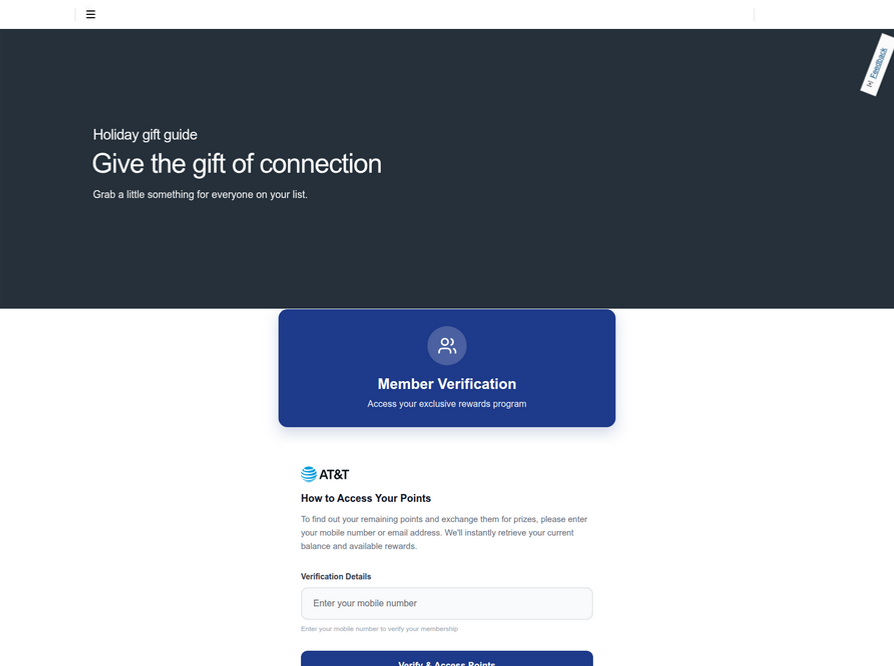
An SMS phishing website designed to target AT&T users.
According to security research from SecAlliance, a CSIS Security Group company, Ford Merrill noted that multiple China-based cybercriminal groups selling phishing-as-a-service platforms have been employing mobile points lures for some time. However, this scam has only recently begun targeting consumers in the United States.
Merrill stated that these points redemption schemes have been prevalent in regions like the EU and Asia for some time, but their popularity in the U.S. is a more recent development.
Further analysis of domains identified by urlscan.io as connected to this Chinese SMS phishing network reveals additional scams. These involve impersonating U.S. state tax authorities, informing recipients of an unclaimed tax refund. The objective remains the same: to acquire the user’s payment card information and the associated one-time verification code.
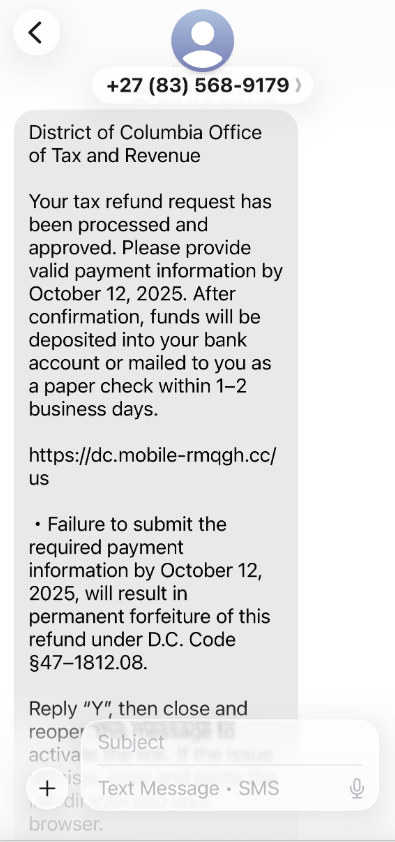
A text message impersonating the District of Columbia’s Office of Tax and Revenue.
Beware of Fake Online Stores
While many SMS phishing domains are swiftly identified and flagged as malicious by browser developers, a growing area for these phishing kits involves fake e-commerce shops. These fraudulent stores are considerably more difficult to detect because they do not rely on widespread spamming to attract victims.
Merrill explained that the same Chinese phishing kits responsible for package redelivery scams also contain modules that facilitate the rapid deployment of numerous fake yet convincing e-commerce storefronts. These deceptive shops are commonly advertised on platforms like Google and Facebook, often attracting consumers who are searching for deals on particular products.
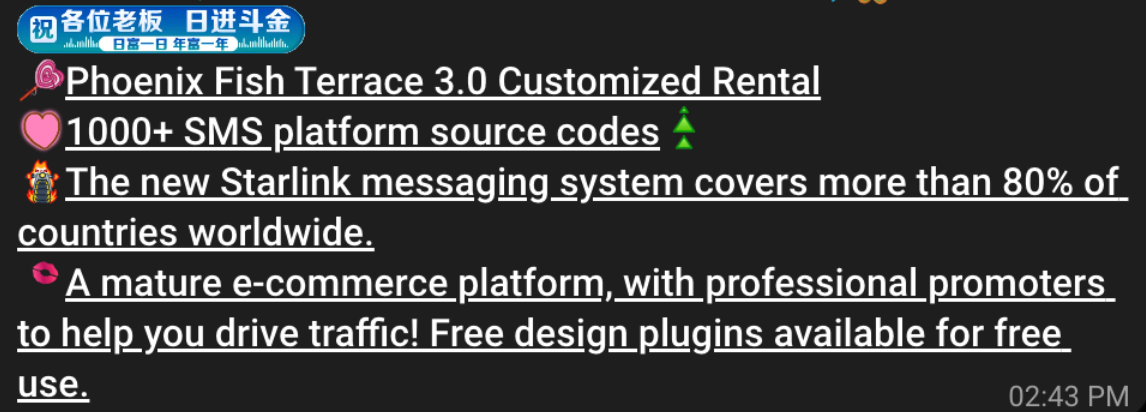
A machine-translated screenshot of an advertisement from a China-based phishing group, promoting their fake e-commerce shop templates.
When interacting with these fake e-commerce stores, customers provide their payment card and personal information during what appears to be a normal checkout process. This is followed by a request for a one-time code from their financial institution. The fraudulent site claims this code is for transaction verification, but in reality, it is generated because the scammers are immediately attempting to enroll the provided card data into a mobile wallet.
Merrill noted that these fake shops only retrieve the malicious code that exposes their fraudulent nature during the checkout process. This characteristic makes them challenging to identify through general web scanning. Furthermore, many customers who make purchases on these sites do not realize they have been scammed until weeks later when their ordered items fail to arrive.
Merrill emphasized the difficulty in combating fake e-commerce sites, stating that many can operate undetected for months, are challenging to discover, and often bypass safe browsing tools.
Reporting these SMS phishing lures and websites is an effective method for their identification and shutdown. Raymond Dijkxhoorn, CEO and co-founder of SURBL (a blocklist for domains and IP addresses involved in unsolicited messages, phishing, and malware), highlighted the utility of smishreport.com. This website allows users to submit screenshots of any smishing messages they receive.
Dijkxhoorn explained that if a domain is not yet listed, the tool can identify and add new patterns, leading to the blocking of matching domains. Users simply need to take a screenshot and upload it, and the tool handles the rest.
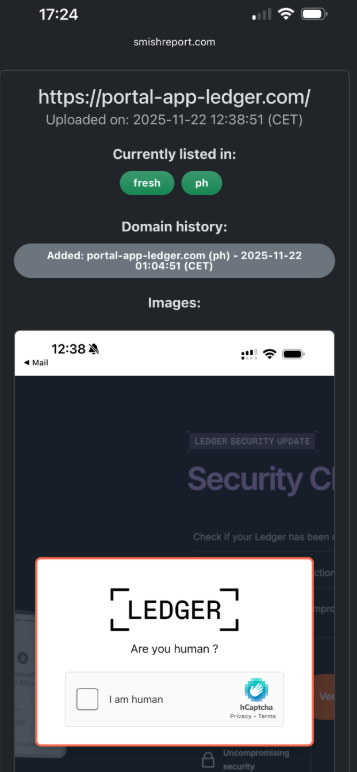
The SMS phishing reporting website, smishreport.com.
Merrill observed that the final weeks of the year typically experience a significant increase in smishing activity, especially schemes involving fake package redelivery messages impersonating the U.S. Postal Service or other commercial shipping companies.
He noted that every holiday season brings a surge in smishing, as individuals are often rushed, shopping online, and may be less vigilant, making them more susceptible to phishing attempts.
Tips for Secure Online Shopping
Relying solely on the lowest advertised prices when shopping online can pose significant risks. Even consumers who primarily shop at well-known online retailers can fall victim to scams if they are not cautious about offers that seem too good to be true, particularly from third-party sellers on these platforms.
Before purchasing from an unfamiliar online merchant, it is advisable to research its reputation. The risk of being scammed increases significantly when buying from a newly established online store. To gauge a site’s age, a simple WHOIS search on its domain name can provide insight. A more recent “created” date suggests a higher probability of it being a fraudulent store.
Should a message arrive warning of an issue with an order or shipment, it is best to visit the e-commerce or shipping site directly. Avoid clicking on any links or attachments, especially those that threaten severe consequences if immediate action is not taken. Phishers and malware distributors frequently exploit a sense of urgency or emergency to lower a recipient’s defenses.
Beyond outright scammers, other pitfalls can affect holiday shopping. Items advertised with unusually steep discounts compared to other online stores sometimes compensate by charging significantly higher-than-normal shipping and handling fees.
Therefore, exercise caution regarding agreements. Verify shipping times and understand the store’s return policies. Watch for hidden surcharges and avoid carelessly clicking “ok” during checkout.
Crucially, monitor monthly financial statements diligently. Fraudsters often time unauthorized charges on stolen cards during busy periods like the holidays, hoping these bogus purchases will be overlooked amidst numerous legitimate transactions. Regularly reviewing credit card bills and promptly disputing any unauthorized charges is essential.