WhatsApp’s Media Handling Strategy
WhatsApp provides default end-to-end encryption for over 3 billion people to message securely each and every day. Online security is an adversarial space, and to continue ensuring users can keep messaging securely, the platform constantly adapts and evolves its strategy against cyber-security threats, all while supporting the WhatsApp infrastructure to help people connect.
For example, WhatsApp, like many other applications, allows users to share media and other types of documents. WhatsApp helps protect users by warning about dangerous attachments like APKs, yet rare and sophisticated malware could be hidden within a seemingly benign file like an image or video. These maliciously crafted files might target unpatched vulnerabilities in the operating system, libraries distributed by the operating system, or the application itself.
To help protect against such potential threats, WhatsApp is increasingly using the Rust programming language, including in its media sharing functionality. Rust is a memory safe language offering numerous security benefits. This is believed to be the largest global rollout of any library written in Rust.
To explain why and how this was rolled out, it is helpful to review a key OS-level vulnerability that signaled the need for hardening media-sharing defenses at WhatsApp.
2015 Android Vulnerability: A Wake-up Call for Media File Protections
In 2015, Android devices and the applications that ran on them became vulnerable to the “Stagefright” vulnerability. The bug lay in the processing of media files by operating system-provided libraries, so WhatsApp and other applications could not patch the underlying vulnerability. Because it could often take months for people to update to the latest version of their software, solutions were sought to keep WhatsApp users safe, even in the event of an operating system vulnerability.
At that time, a cross-platform C++ library already developed by WhatsApp to send and consistently format MP4 files (called “wamedia”) was identified as modifiable to detect files which do not adhere to the MP4 standard and might trigger bugs in a vulnerable OS library on the receiver side – hence putting a target’s security at risk. This check was implemented and was able to protect WhatsApp users from the Stagefright vulnerability much more rapidly than by depending on users to update the OS itself.
However, because media checks run automatically on download and process untrusted inputs, it was identified early on that wamedia was a prime candidate for using a memory safe language.
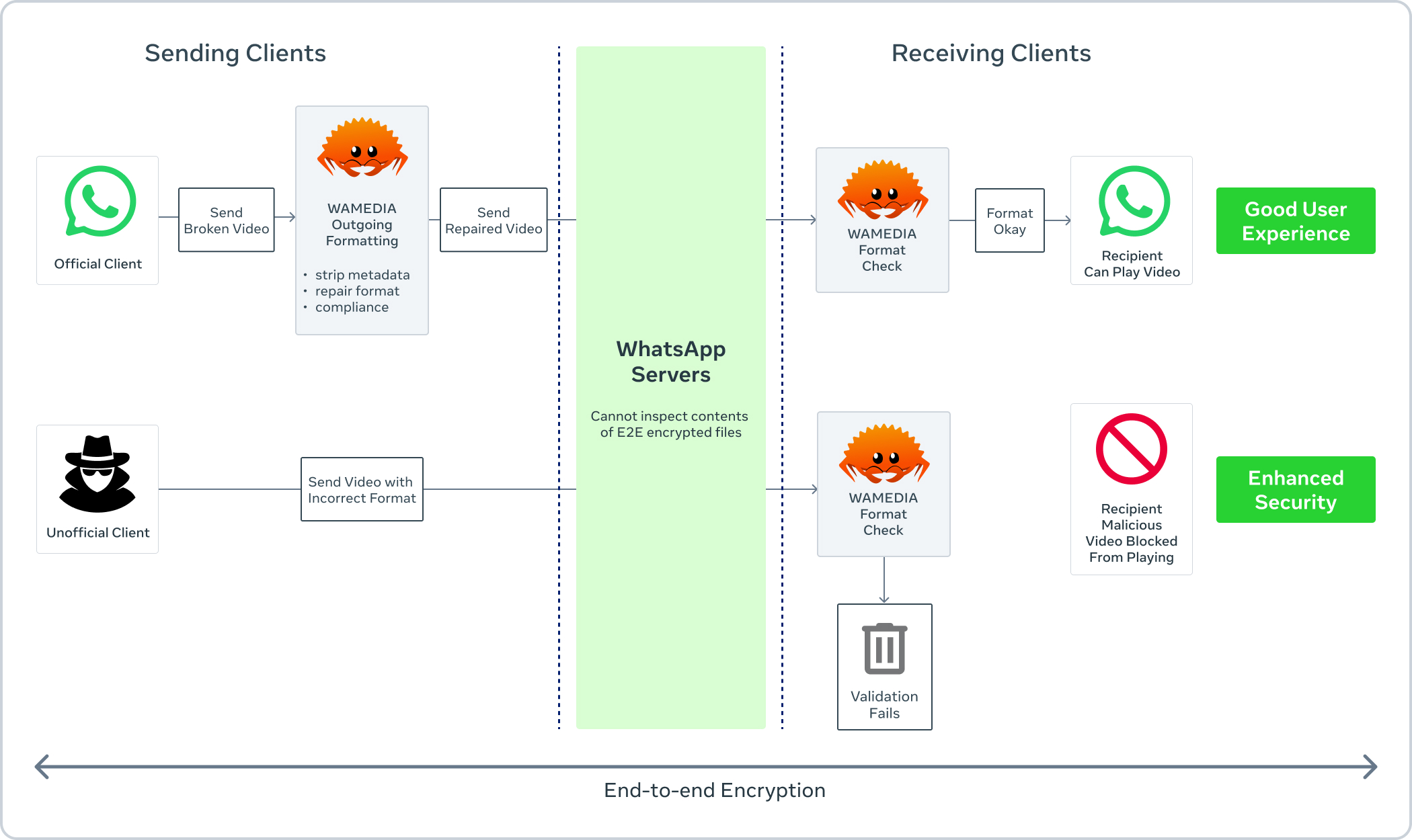
The Rust at Scale Solution
Rather than an incremental rewrite, the Rust version of wamedia was developed in parallel with the original C++ version. Differential fuzzing and extensive integration and unit tests were used to ensure compatibility between the two implementations.
Two major hurdles included the initial binary size increase due to bringing in the Rust standard library and the build system support required for the diverse platforms supported by WhatsApp. A long-term commitment was made by WhatsApp to build that support. In the end, 160,000 lines of C++ (excluding tests) were replaced with 90,000 lines of Rust (including tests). The Rust version showed performance and runtime memory usage advantages over the C++. Given this success, Rust was fully rolled out to all WhatsApp users and many platforms: Android, iOS, Mac, Web, Wearables, and more. With this positive evidence, memory safe languages are expected to play an ever increasing part in WhatsApp’s overall approach to application and user security.
Over time, more checks have been added for non-conformant structures within certain file types to help protect downstream libraries from parser differential exploit attempts. Additionally, higher risk file types, even if structurally conformant, are checked for risk indicators. For instance, PDFs are often a vehicle for malware, and more specifically, the presence of embedded files and scripting elements within a PDF further raise risks. The system also detects when one file type masquerades as another, through a spoofed extension or MIME type. Finally, known dangerous file types, such as executables or applications, are uniformly flagged for special handling in the application UX. Altogether, this ensemble of checks is called “Kaleidoscope.” This system protects people on WhatsApp from potentially malicious unofficial clients and attachments. Although format checks will not stop every attack, this layer of defense helps mitigate many of them.
Each month, these libraries are distributed to billions of phones, laptops, desktops, watches, and browsers running on multiple operating systems for people on WhatsApp, Messenger, and Instagram. This is the largest ever deployment of Rust code to a diverse set of end-user platforms and products known. This experience demonstrates the production-readiness and unique value proposition of Rust on the client-side.
How Rust Fits Into WhatsApp’s Approach to App Security
This is just one example of WhatsApp’s many investments in security. This includes the implementation of default end-to-end encryption for personal messages and calls, offering end-to-end encrypted backups, and using key transparency technology to verify a secure connection, providing additional calling protections, and more.
WhatsApp has a strong track record of transparency when issues are found and works to hold bad actors accountable. For example, WhatsApp reports CVEs for important issues found in its applications, even if no evidence of exploitation is discovered. This is done to provide users the best chance of protecting themselves by seeing a security advisory and updating quickly.
To ensure application security, identifying and quantifying risk sources is essential. This is achieved through internal and external audits like NCC Group’s public assessment of WhatsApp’s end-to-end encrypted backups, fuzzing, static analysis, supply chain management, and automated attack surface analysis. The Bug Bounty program was also recently expanded to introduce the WhatsApp Research Proxy – a tool that makes research into WhatsApp’s network protocol more effective.
Next, identified risk is reduced. Like many others in the industry, it was found that the majority of the high severity vulnerabilities published were due to memory safety issues in code written in the C and C++ programming languages. To combat this, three parallel strategies are pursued:
- Design the product to minimize unnecessary attack surface exposure.
- Invest in security assurance for the remaining C and C++ code.
- Default the choice of memory safe languages, and not C and C++, for new code.
Protections have been added by WhatsApp, such as CFI, hardened memory allocators, safer buffer handling APIs, and more. C and C++ developers receive specialized security training, development guidelines, and automated security analysis on their changes. Strict SLAs are also in place for fixing issues uncovered by the risk identification process.
Accelerating Rust Adoption to Enhance Security
Rust enabled WhatsApp’s security team to develop a secure, high performance, cross-platform library to ensure media shared on the platform is consistent and safe across devices. This is an important step forward in adding additional security behind the scenes for users and part of an ongoing defense-in-depth approach. Security teams at WhatsApp and Meta are highlighting opportunities for high impact adoption of Rust to interested teams, and an acceleration of Rust adoption is anticipated over the coming years.