A critical internet-wide security vulnerability has been actively exploited for several months, necessitating increased awareness of the threat. The security of internal networks behind internet routers may no longer be as robust as previously assumed.
Security firm Synthient reports over 2 million Kimwolf-infected devices worldwide, with significant numbers in Vietnam, Brazil, India, Saudi Arabia, Russia, and the United States. Synthient’s analysis indicates that two-thirds of these infections are Android TV boxes lacking inherent security or authentication.
A new botnet, named Kimwolf, has seen explosive growth recently, infecting over 2 million devices globally. This malware compels compromised systems to transmit malicious internet traffic, including ad fraud, account takeover attempts, and extensive content scraping. It also facilitates powerful distributed denial-of-service (DDoS) attacks that can disable websites for extended periods.
Beyond its considerable scale, Kimwolf’s rapid propagation method is particularly concerning. It achieves this by tunneling through various “residential proxy” networks, gaining access to the local networks of proxy endpoints and infecting devices that are typically protected by firewalls and internet routers.
Residential proxy networks offer users the ability to anonymize and localize their web traffic to specific geographic regions. The largest of these services enable traffic routing through devices located almost anywhere globally.
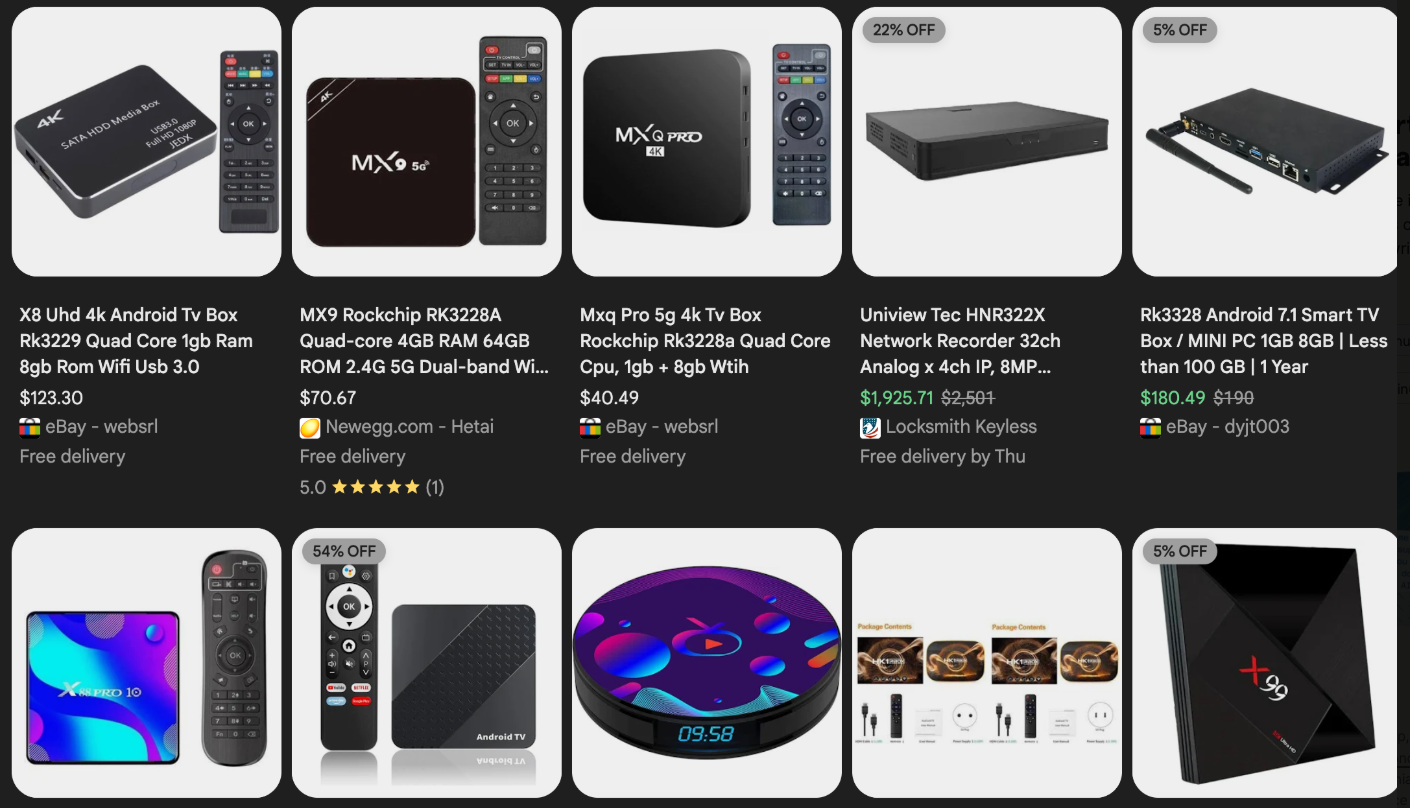
Malware that transforms a user’s internet connection into a proxy node is frequently bundled with questionable mobile applications and games. These residential proxy programs are also often pre-installed on unofficial Android TV boxes sold by third-party vendors on major e-commerce platforms such as Amazon, BestBuy, Newegg, and Walmart.
These TV boxes, priced between $40 and $400, are sold under numerous obscure brands and model numbers. They are often advertised as a means to stream subscription video content for free. However, this convenience comes with a hidden cost: these devices account for a significant portion of the estimated two million systems currently infected with Kimwolf.
Examples of unsanctioned Android TV boxes that include pre-installed residential proxy malware. Image: Synthient.
The Kimwolf botnet also effectively infects various internet-connected digital photo frames, which are widely available on major e-commerce sites. In November 2025, Quokka researchers released a report (PDF) outlining significant security flaws in Android-based digital picture frames utilizing the Uhale app, including Amazon’s top-selling digital frame as of March 2025.
These photo frames and unofficial Android TV boxes present two primary security concerns. Firstly, a significant number are shipped with pre-installed malware, or they necessitate downloading an unofficial Android App Store and associated malware for the device’s intended use (video content piracy). These unwanted programs typically transform the device into a residential proxy node, which is then resold.
Secondly, these devices often utilize internet-connected microcomputer boards that lack inherent security or authentication features. This means that if a device is on the same network as one or more of these vulnerable units, it may be possible to compromise them concurrently with a single network command.
THERE’S NO PLACE LIKE 127.0.0.1
These security issues became prominent in October 2025 when a computer science undergraduate at the Rochester Institute of Technology started monitoring Kimwolf’s expansion and communicating daily with its presumed operators.
Benjamin Brundage, 22, founded the security firm Synthient, which assists companies in identifying and understanding the misuse of proxy networks. Brundage’s research into Kimwolf, conducted while preparing for final exams, led him to suspect in late October 2025 that it was an Android-based version of Aisuru, a botnet erroneously linked to several major DDoS attacks the previous fall.
Brundage noted that Kimwolf expanded rapidly by exploiting a significant vulnerability in many leading residential proxy services. This weakness stemmed from these services’ insufficient measures to prevent customers from forwarding requests to the internal servers of individual proxy endpoints.
Typically, proxy services implement basic protections to prevent customers from accessing the local networks of proxy endpoints. This involves denying requests for local addresses defined in RFC-1918, such as the common Network Address Translation (NAT) ranges: 10.0.0.0/8, 192.168.0.0/16, and 172.16.0.0/12. These ranges enable multiple devices within a private network to share a single public IP address for internet access, meaning most home or office networks operate within these NAT ranges.
However, Brundage found that Kimwolf operators had devised a method to communicate directly with devices on the internal networks of millions of residential proxy endpoints. This was achieved by altering their Domain Name System (DNS) settings to align with RFC-1918 address ranges.
“Existing domain restrictions can be bypassed using DNS records that point to 192.168.0.1 or 0.0.0.0,” Brundage stated in a security advisory issued to nearly a dozen residential proxy providers in mid-December 2025. “This allows an attacker to send crafted requests to the current device or another device on the local network. This capability is actively being exploited, with attackers using it to deploy malware.”
Similar to the digital photo frames, many residential proxy services operate on mobile devices running games, VPNs, or other applications that contain a hidden component. This component transforms the user’s mobile phone into a residential proxy, frequently without explicit consent.
According to a report published by Synthient, primary actors associated with Kimwolf have been observed profiting from the botnet through app installations, selling residential proxy bandwidth, and offering its DDoS capabilities.
The report noted, “Synthient anticipates increasing interest among threat actors in gaining unrestricted access to proxy networks for device infection, network access, or sensitive information retrieval.” It added, “Kimwolf underscores the dangers of unsecured proxy networks and their potential as an attack vector.”
ANDROID DEBUG BRIDGE
After acquiring several unofficial Android TV box models frequently associated with the Kimwolf botnet, Brundage determined that the proxy service vulnerability was only one factor in Kimwolf’s rapid expansion. He also found that nearly all tested devices were shipped with Android Debug Bridge (ADB) mode enabled by default.

Numerous unofficial Android TV boxes compromised by Kimwolf often display the disclaimer: “Made in China. Overseas use only.” Image: Synthient.
ADB is a diagnostic tool designed exclusively for manufacturing and testing, enabling remote configuration and firmware updates (potentially malicious). However, devices shipped with ADB enabled pose a significant security risk, as they continuously listen for and accept unauthenticated connection requests.
For instance, executing “adb connect” in a command prompt, followed by a vulnerable device’s local IP address and “:5555”, can rapidly grant unrestricted “super user” administrative access.
By early December, Brundage had observed a direct correlation between new Kimwolf infections and proxy IP addresses rented from China-based IPIDEA, which is reportedly the world’s largest residential proxy network.
“Kimwolf nearly doubled in size within a week, solely by exploiting IPIDEA’s proxy pool,” Brundage stated in early December while preparing to inform IPIDEA and ten other proxy providers about his findings.
Synthient confirmed on December 1, 2025, that Kimwolf botnet operators were tunneling through IPIDEA’s proxy network into the local networks of systems running IPIDEA’s proxy software. Attackers deployed malware by directing infected systems to a specific internet address and using the passphrase “krebsfiveheadindustries” to initiate the malicious download.
By December 30, Synthient was monitoring approximately 2 million IPIDEA addresses exploited by Kimwolf in the preceding week. Brundage observed Kimwolf’s rapid recovery after a recent takedown attempt on its control servers, rebuilding from almost zero to two million infected systems within days by exploiting IPIDEA’s proxy endpoints.
IPIDEA reportedly possesses an extensive supply of new proxies, having advertised access to over 100 million residential proxy endpoints worldwide in a single week. Synthient’s analysis of exposed devices within IPIDEA’s proxy pool revealed that over two-thirds were Android devices vulnerable to compromise without authentication.
SECURITY NOTIFICATION AND RESPONSE
Following the discovery of a strong correlation between Kimwolf-infected IP addresses and those offered by IPIDEA, Brundage intended to publicize his findings. The vulnerability had been exploited for months, seemingly by only a few cybercriminals. However, he recognized that public disclosure without allowing vulnerable proxy providers time to address the issue could lead to widespread abuse by more cybercriminal groups.
On December 17, Brundage issued a security notification to all 11 seemingly affected proxy providers, aiming to give them several weeks to acknowledge and fix the issues outlined in his report before public disclosure. Many recipients were IPIDEA resellers operating under their own brands.
In October 2025, IPIDEA was contacted for comment regarding reports that its proxy network seemed to benefit from the emergence of the Aisuru botnet. Aisuru’s operators reportedly transitioned from primarily using the botnet for DDoS attacks to installing IPIDEA’s proxy software, among other programs.
On December 25, an IPIDEA employee, identified as “Oliver,” responded via email, refuting claims that IPIDEA had profited from the Aisuru botnet’s activities.
Oliver stated, “After comprehensively verifying IP traceability records and supplier cooperation agreements, no association was found between any of our IP resources and the Aisuru botnet. Furthermore, no notifications have been received from authoritative institutions regarding our IPs being involved in malicious activities.” Oliver added that for external collaborations, a three-level review mechanism is implemented for suppliers, encompassing qualification verification, resource legality authentication, and continuous dynamic monitoring, to ensure compliance throughout the cooperation process.
Oliver further asserted that “IPIDEA firmly opposes all forms of unfair competition and malicious smearing in the industry, always participates in market competition with compliant operation and honest cooperation, and also calls on the entire industry to jointly abandon irregular and unethical behaviors and build a clean and fair market ecosystem.”
Concurrently with Oliver’s email, Brundage received and shared a response from IPIDEA’s security officer, identified as Byron. Byron indicated that IPIDEA had implemented significant security modifications to its residential proxy service to address the vulnerability detailed in Brundage’s report.
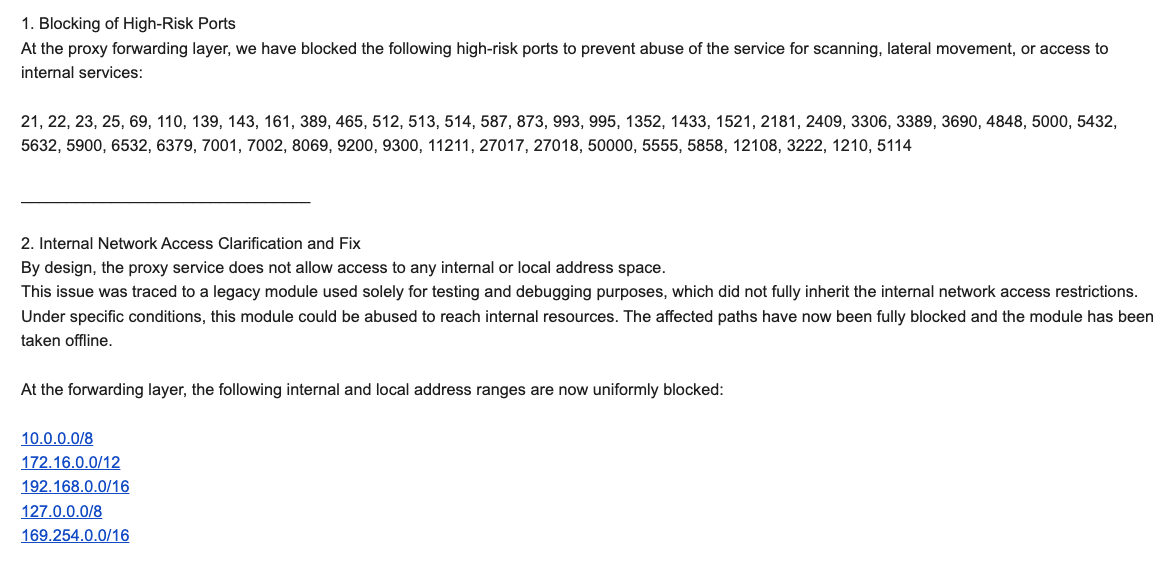
Byron clarified, “By design, the proxy service does not permit access to any internal or local address space. This issue was traced to a legacy module used exclusively for testing and debugging, which did not fully inherit internal network access restrictions. Under specific conditions, this module could be exploited to access internal resources. The affected paths have now been fully blocked, and the module has been taken offline.”
Byron informed Brundage that IPIDEA also implemented several mitigations to block DNS resolution to internal (NAT) IP ranges. Additionally, proxy endpoints are now prevented from forwarding traffic on “high-risk” ports to “prevent abuse of the service for scanning, lateral movement, or access to internal services.”
An excerpt from an email sent by IPIDEA’s security officer in response to Brundage’s vulnerability notification.
Brundage indicated that IPIDEA seems to have successfully patched the identified vulnerabilities. He also noted that Kimwolf actors were not observed targeting proxy services other than IPIDEA, which has not provided further comment.
Riley Kilmer, founder of Spur.us, a technology firm specializing in identifying and filtering proxy traffic, confirmed Brundage’s findings. Kilmer stated that Spur’s tests verified IPIDEA and its affiliate resellers provided full, unfiltered access to the local LAN.
Kilmer highlighted that a particularly popular model of unsanctioned Android TV box, the Superbox (previously discussed in November’s Is Your Android TV Streaming Box Part of a Botnet?), leaves Android Debug Mode active on localhost:5555.
Kilmer explained, “Since Superbox converts the IP into an IPIDEA proxy, a malicious actor can simply use the proxy to access localhost on that port and install any undesirable SDKs [software development kits].”
Superbox media streaming boxes available on Walmart.com.
ECHOES FROM THE PAST
Brundage and Kilmer suggest that IPIDEA may be a successor to 911S5 Proxy, a residential proxy network active from 2014 to 2022 and widely used in cybercrime communities. 911S5 Proxy collapsed a week after a detailed investigation into its questionable origins and Chinese leadership was published.
A 2022 profile referenced research by the University of Sherbrooke in Canada, which examined the potential threat 911S5 posed to internal corporate networks. Researchers observed that “the infection of a node enables the 911S5 user to access shared resources on the network such as local intranet portals or other services.”
The researchers further explained, “It also enables the end user to probe the LAN network of the infected node. Using the internal router, it would be possible to poison the DNS cache of the LAN router of the infected node, enabling further attacks.”
In 2022, 911S5 initially responded to reports by claiming an internal security review was underway. However, the proxy service abruptly ceased operations a week later, citing a malicious hacker’s destruction of all customer and payment records. In July 2024, the U.S. Department of the Treasury sanctioned the alleged creators of 911S5, and the U.S. Department of Justice arrested the Chinese national identified in the 2022 profile of the service.
Kilmer noted that IPIDEA also runs a related service, 922 Proxy, which has been marketed as a direct alternative to 911S5 Proxy since its inception.
Kilmer commented, “The naming choice clearly indicates an intent to attract former 911S5 customers.”
Oxylabs, a major proxy provider, was among those who received Synthient’s notification. Brundage shared an email from Oxylabs’ security team on December 31, confirming that the company had begun implementing security modifications to address the vulnerabilities detailed in Synthient’s report.
When contacted, Oxylabs confirmed implementing changes that “now eliminate the ability to bypass the blocklist and forward requests to private network addresses using a controlled domain.” However, the company stated there was no evidence that Kimwolf or other attackers had exploited its network.
The Oxylabs statement further noted, “In parallel, the domains identified in the reported exploitation activity were reviewed, and no associated traffic was observed.” Based on this review, there was “no indication that our residential network was impacted by these activities.”
PRACTICAL IMPLICATIONS
Consider a scenario where simply allowing someone to use a Wi-Fi network could result in a Kimwolf botnet infection. If a friend or family member uses a Wi-Fi network, unaware that their mobile phone is infected with an app that converts it into a residential proxy node, the home’s public IP address could then become available for rent on a residential proxy provider’s website.
Malicious actors, such as those behind Kimwolf, can then utilize online residential proxy services to access that proxy node via the IP address. They tunnel through it into the local area network (LAN) and automatically scan the internal network for devices with Android Debug Bridge mode enabled.
After a guest departs and disconnects from a Wi-Fi network, two devices on the local network—a digital photo frame and an unsanctioned Android TV box—could be infected with Kimwolf. These devices, though never intended for direct internet exposure, become compromised.
Another potential scenario involves attackers leveraging proxy network access to alter an internet router’s settings, redirecting it to malicious DNS servers under their control. This would allow them to dictate where a web browser navigates when requesting a website. This concept is not unprecedented; the DNSChanger malware in 2012 infected over half a million routers with search-hijacking malware, leading to the formation of a dedicated security industry working group for its containment and eradication.
XLAB
Much of the current information on Kimwolf originates from the Chinese security firm XLab, which initially documented the Aisuru botnet’s emergence in late 2024. In its recent blog post, XLab reported beginning to track Kimwolf on October 24, when its control servers overwhelmed Cloudflare’s DNS servers with lookups for the unique domain 14emeliaterracewestroxburyma02132[.]su.
This domain, along with others linked to early Kimwolf variants, spent several weeks at the top of Cloudflare’s list of most requested internet domains, surpassing Google.com and Apple.com. This occurred because Kimwolf instructed its millions of bots to frequently check in via Cloudflare’s DNS servers during that period.

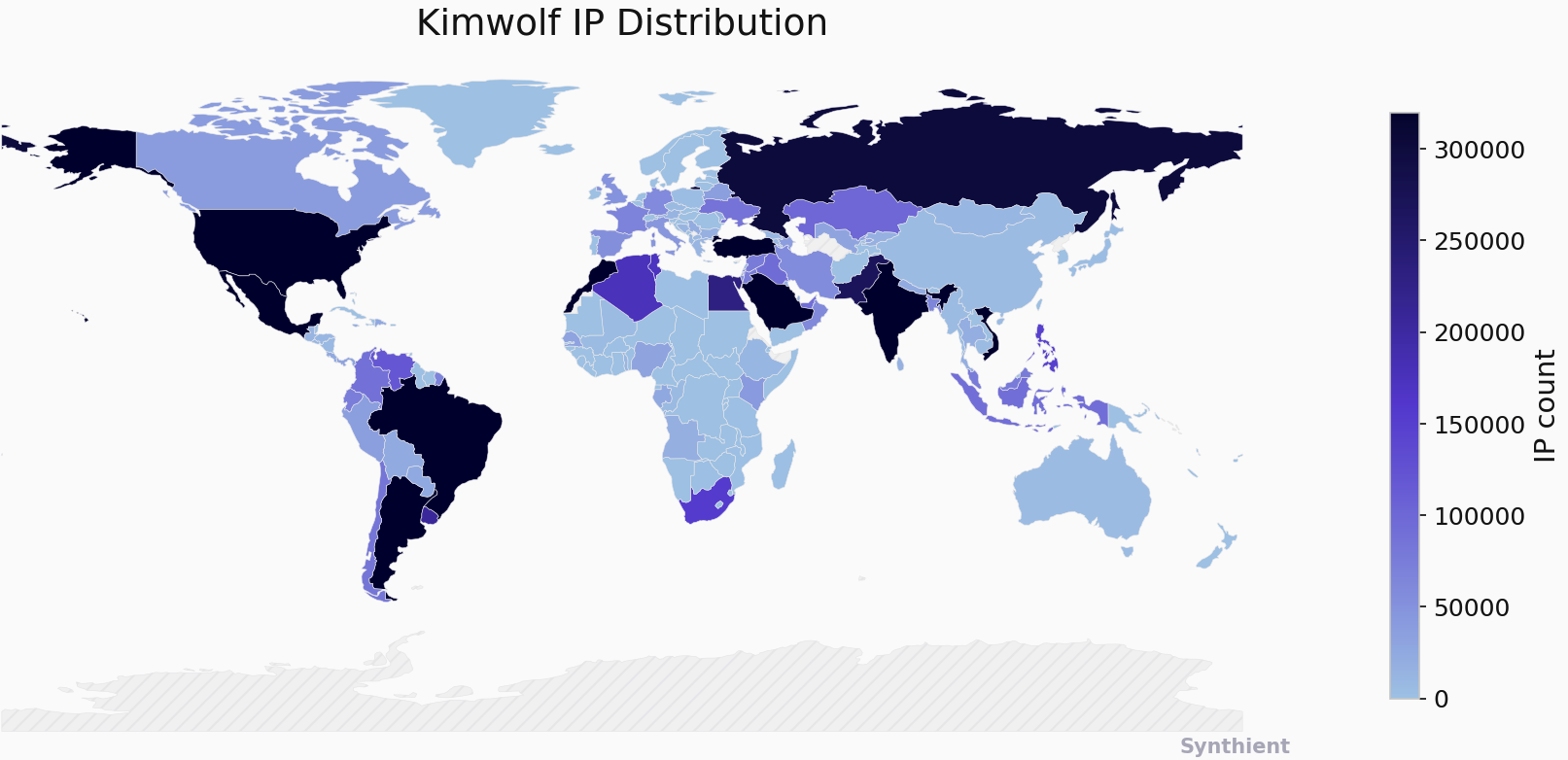
Chinese security firm XLab estimated the Kimwolf botnet had compromised between 1.8 and 2 million devices, with significant concentrations in Brazil, India, the United States, and Argentina. Image: blog.xLab.qianxin.com
The XLab report clarifies that some of Kimwolf’s early activities were likely incorrectly attributed to the Aisuru botnet, which appears to be managed by a separate entity. While IPIDEA may have been accurate in denying affiliation with Aisuru, Brundage’s data strongly indicated that its proxy service was extensively exploited by Kimwolf, Aisuru’s Android variant.
XLab reported that Kimwolf has infected at least 1.8 million devices, and has shown it is able to rebuild itself quickly from scratch.
XLab researchers stated, “Analysis indicates that Kimwolf’s primary infection targets are TV boxes deployed in residential network environments. Since residential networks usually adopt dynamic IP allocation mechanisms, the public IPs of devices change over time, so the true scale of infected devices cannot be accurately measured solely by the quantity of IPs. In other words, the cumulative observation of 2.7 million IP addresses does not equate to 2.7 million infected devices.”
Measuring Kimwolf’s size is also challenging due to infected devices being spread across various global time zones. The blog post noted, “Affected by time zone differences and usage habits (e.g., turning off devices at night, not using TV boxes during holidays, etc.), these devices are not online simultaneously, further increasing the difficulty of comprehensive observation through a single time window.”
XLab observed that the Kimwolf author displayed an “obsessive fixation,” seemingly embedding “easter eggs” related to the article’s original author’s name in various parts of the botnet’s code and communications.
Image: XLAB.
ANALYSIS AND ADVICE
A challenging aspect of threats like Kimwolf is the difficulty for average users to ascertain if devices on their internal network are vulnerable to such threats or already infected with residential proxy malware.
Even if one could identify residential proxy activity on an internal network linked to a specific mobile device, the next step would involve isolating and removing the application or component responsible for transforming the device into a residential proxy.
The necessary tools and expertise for this level of network visibility are generally unavailable to the average consumer. Configuring a network to monitor and interpret all incoming and outgoing traffic logs typically exceeds the technical skills of most internet users, and even many security experts.
Synthient offers a website page where visitors can check if their public internet address has been associated with Kimwolf-infected systems. Brundage has also compiled a list of unofficial Android TV boxes most frequently observed within the Kimwolf botnet.
If a TV box matches any of these identified model names or numbers, it is advisable to remove it from the network. Should such a device be found on a family member’s or friend’s network, sharing this information and explaining the potential risks of keeping it connected is recommended.
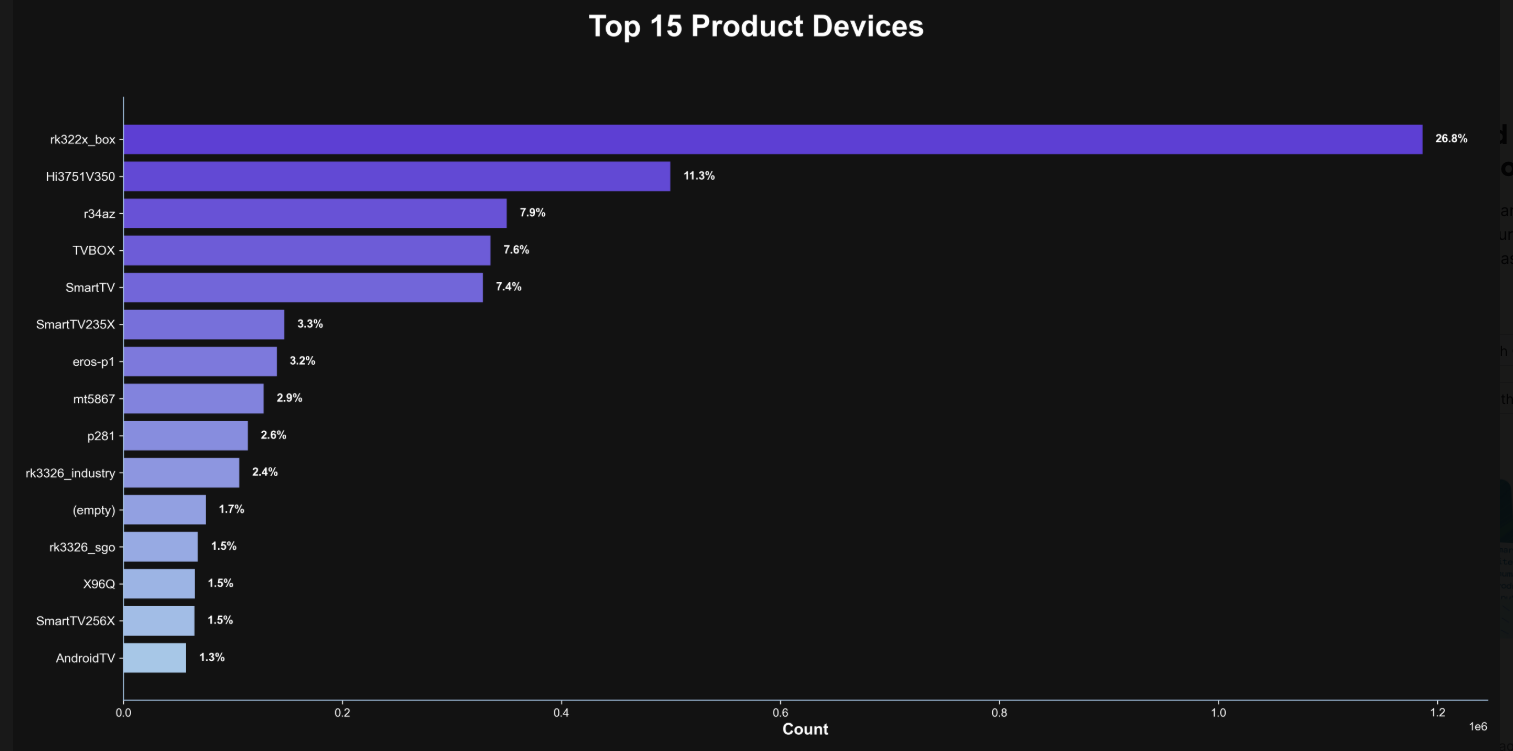
Synthient’s list of the top 15 product devices found in the Kimwolf botnet.
Chad Seaman, a principal security researcher at Akamai Technologies, advocates for increased consumer caution regarding these unofficial Android TV boxes, encouraging their complete avoidance.
Seaman stated, “Consumers should be highly cautious of these inferior devices and residential proxy schemes. It is crucial to emphasize their danger to both individuals and the broader community. The outdated security model, which assumes a Local Internal Network (LAN) is inherently safe from malicious actors, is no longer valid.”
Seaman added, “The notion that an application can facilitate this kind of abuse on one’s network and others should prompt careful consideration regarding which devices are permitted on a local network. This issue extends beyond Android devices, as some proxy services offer SDKs for Mac, Windows, and iPhone, potentially allowing software to inadvertently expose a network to numerous unauthorized individuals.”
In July 2025, Google initiated a “John Doe” lawsuit (PDF) against 25 unnamed defendants, collectively known as the “BadBox 2.0 Enterprise.” Google described this as a botnet comprising over ten million unauthorized Android streaming devices involved in advertising fraud. The BADBOX 2.0 botnet, according to Google, not only compromises various device types before purchase but can also infect devices by requiring downloads of malicious apps from unofficial marketplaces.
Google’s lawsuit followed a June 2025 advisory from the Federal Bureau of Investigation (FBI). The FBI warned that cybercriminals were gaining unauthorized access to home networks by pre-configuring products with malware or infecting devices during setup when required applications containing backdoors were downloaded.
The FBI reported that BADBOX 2.0 was identified subsequent to the disruption of the original BADBOX campaign in 2024. The initial BADBOX, discovered in 2023, primarily involved Android devices compromised with backdoor malware before being sold.
Lindsay Kaye, vice president of threat intelligence at HUMAN Security, a company involved in the BADBOX investigations, stated that the BADBOX botnets and associated residential proxy networks were detected due to their extensive involvement in advertising fraud, ticket scalping, retail fraud, account takeovers, and content scraping.
Kaye advises consumers to opt for established brands when purchasing devices requiring wired or wireless connections.
Kaye suggested, “To avoid becoming victims of proxies, it is safest to stick with name brands. Anything promising something for free or low-cost, or offering something for nothing, is generally not worth the risk. Additionally, users should exercise caution regarding the applications they permit on their phones.”
Modern wireless routers often facilitate the quick setup of a “Guest” wireless network. This feature allows guests to access the internet while preventing their devices from communicating with other local network devices, such as shared folders, printers, and drives. When granting network access to a friend, family member, or contractor, using the guest Wi-Fi network credentials is a recommended option.
A small but vocal group, often advocating for piracy, tends to dismiss the security threats associated with unsanctioned Android TV boxes. These individuals object to the idea of discarding such devices, often arguing that internet-connected devices are inherently neutral and that even factory-infected boxes can be reflashed with new firmware or custom ROMs free of malicious software.
However, it is important to note that most purchasers of these devices are not security or hardware experts. These devices are appealing because they promise valuable content for “free.” Many buyers are unaware of the risks they incur by connecting these questionable TV boxes to their networks.
It is noteworthy that the entertainment industry has not yet exerted more visible pressure on major e-commerce vendors to cease selling this insecure and actively malicious hardware, which is largely produced and marketed for video piracy. These TV boxes are a public nuisance due to their bundled malicious software and lack of inherent security or authentication, making them appealing targets for cybercriminals.