Firefox’s security model fundamentally relies on process separation. Rather than operating as a single entity, Firefox uses multiple processes, each with distinct privileges, communicating through Inter-Process Communication (IPC). For instance, tasks like loading, processing, and rendering a website occur within an isolated Content Process, which operates under a highly restrictive sandbox. Conversely, critical actions such as file system access are exclusively handled by the Parent Process.
Executing potentially malicious code with reduced privileges helps to lessen the impact of any code execution vulnerability. To achieve complete control, an attacker must then discover a secondary vulnerability that enables bypassing these privilege limitations, a technique commonly referred to as a “sandbox escape.”
An attacker typically has two primary methods to achieve a sandbox escape. One approach involves directly attacking the underlying operating system from within a compromised content process. As all processes must interact with the operating system for various functions, an attacker might target vulnerabilities in these interfaces to escalate privileges.
With changes already implemented in Firefox that significantly restrict the operating system interfaces accessible to low-privilege processes, the second attack vector gains prominence: exploiting vulnerabilities in privileged IPC endpoints. Because low-privilege content processes must communicate with the privileged parent process, the parent necessarily exposes specific interfaces.
Should these interfaces lack adequate security checks or contain memory safety flaws, a content process could potentially exploit them. This exploitation might allow the process to execute actions with elevated privileges, potentially resulting in a complete takeover of the parent process.
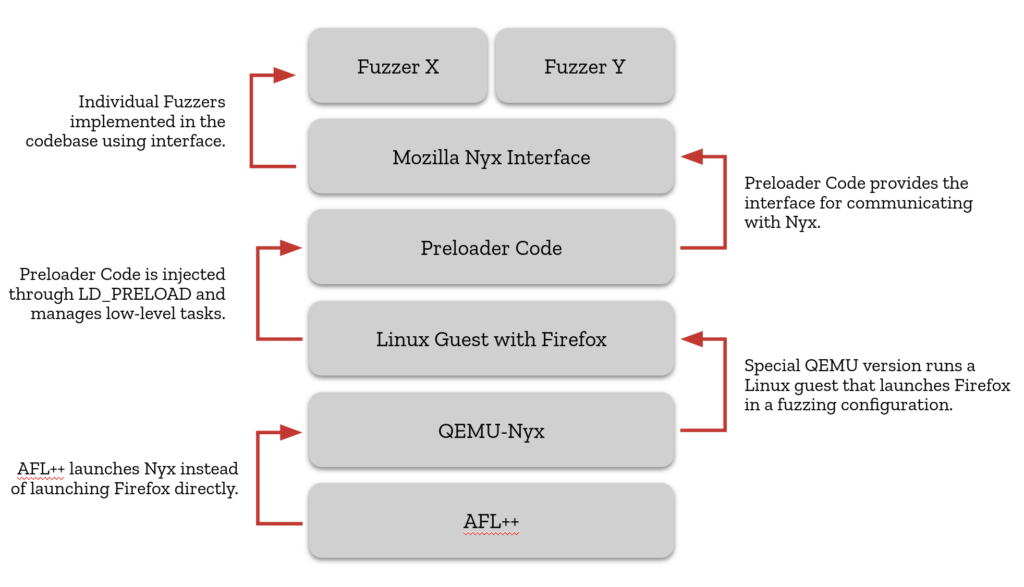
Fuzzing has historically been a successful method for Mozilla, uncovering various issues, including security vulnerabilities within its codebase. Nevertheless, applying fuzzing to critical IPC interfaces has consistently presented challenges. This difficulty stems mainly from the fact that IPC interfaces cannot be tested in isolation, necessitating a full browser environment for testing. Additionally, improper use of IPC interfaces can trigger browser restarts, introducing significant latency between fuzzing iterations.
To address this challenge, collaboration with the research community led to the adoption of a novel method for rewinding application state during fuzzing. Initial successes with this technique emerged in 2021, utilizing an experimental prototype that eventually evolved into the open-source snapshot fuzzing tool named “Nyx”.
As of 2024, various snapshot fuzzing targets for IPC are now operational in production. Snapshot fuzzing represents a relatively new technology that has gained traction in recent years, and its transition from a theoretical concept to practical application has been a significant achievement.
This technology has already facilitated the identification and resolution of several potential issues within the IPC layer. Efforts to enhance testing will continue, aiming to deliver the most secure version of Firefox.