
Messenger has introduced key transparency verification for end-to-end encrypted chats, enhancing conversation security. This feature provides further assurance that only participants can access messages, preventing unauthorized access, including by Meta.
End-to-end encryption on Messenger already secures direct messages and calls. The platform also emphasizes the importance of verifying that public keys, used for encryption, belong to the intended recipients and remain untampered.
This development draws on industry experience, particularly WhatsApp’s 2023 key transparency implementation, which proved its viability for large-scale encrypted messaging. Messenger’s solution extends these efforts, offering a robust and reliable system with comparable security.
What Is Key Transparency?
Key transparency offers users a verifiable record of public keys, enabling confirmation that conversations are encrypted with the correct keys for their contacts and that no malicious key swaps have occurred. This increases confidence that messages are only accessible to intended recipients.
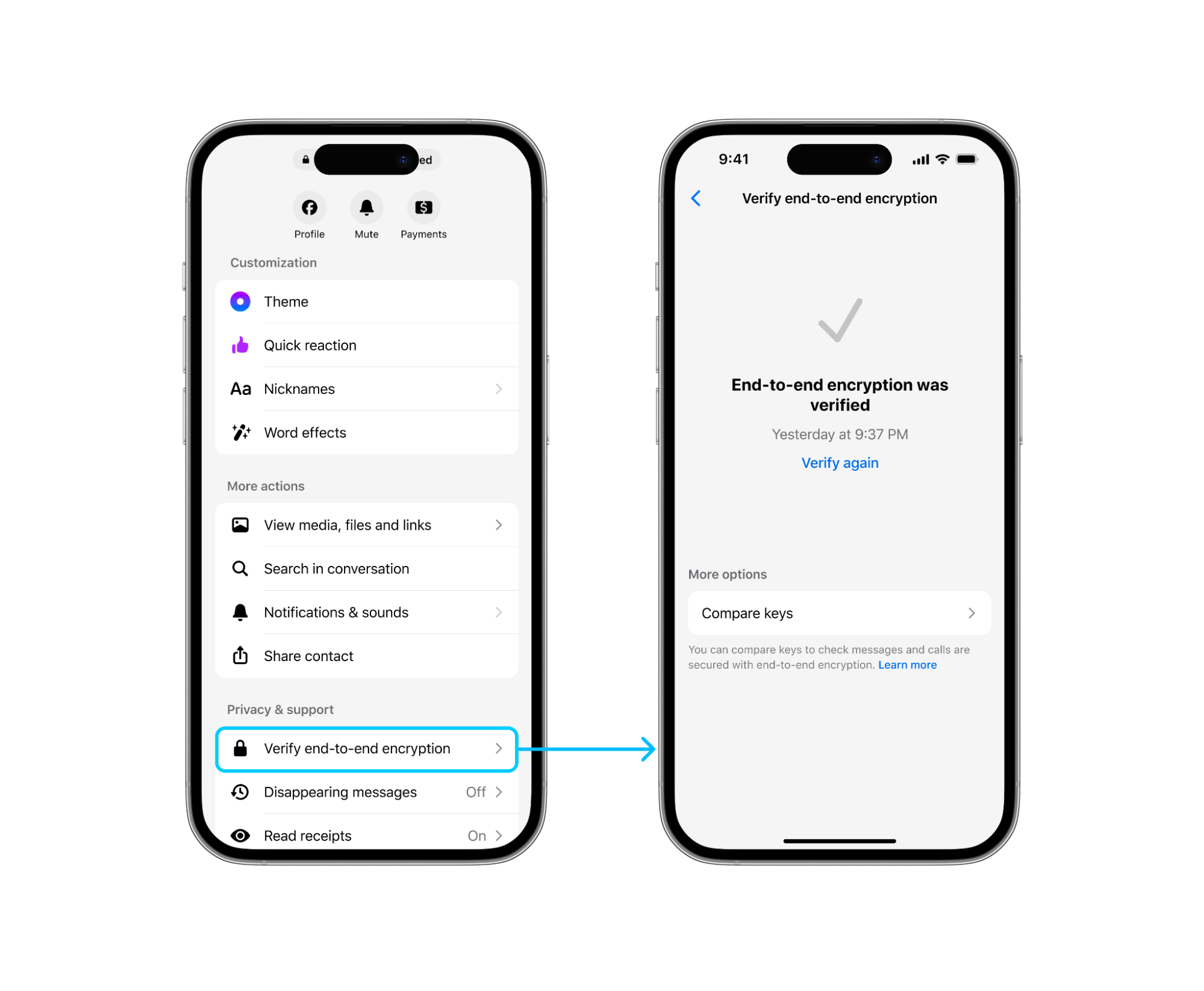
Users can currently check keys for end-to-end encrypted chats on Messenger, but this process can be inconvenient, especially for those using multiple devices, each with its own key. Key changes also occur when new devices are added or re-registered, requiring repeated checks.
To simplify this, a new key transparency-based security feature has been introduced, allowing automatic key verification without manual comparison. Manual verification remains an option for users who prefer it.
How We’re Handling Messenger Keys at Scale
Messenger’s key transparency uses the Auditable Key Directory (AKD) library, similar to WhatsApp’s system, for secure distribution and verification of public keys. Cloudflare’s key transparency auditor adds another layer of verification, ensuring transparent and auditable key distribution. Cloudflare’s auditor provides a live log for both the WhatsApp and Messenger directories on the Key Transparency Dashboard.
Implementing key transparency for Messenger’s scale posed unique engineering challenges, primarily due to the high volume and frequency of key updates. Messenger indexes keys for every logged-in device, resulting in individual users often having multiple, dynamic keys.
This complexity results in frequent key updates within the key transparency directory. Epochs are published approximately every 2 minutes, with hundreds of thousands of new keys added per epoch. The database has grown to billions of key entries since indexing began. Several infrastructure and library advancements have been implemented to manage this growing dataset, ensuring high availability and real-time verification:
Algorithmic efficiency for key lookup and verification in the AKD library was improved by optimizing for smaller proof sizes, even with increasing key updates. Previously, proof sizes grew linearly with the transparency tree’s height, which was challenging to manage given the number of nodes.
Existing infrastructure was updated to enhance resilience against temporary outages and improve recovery from key sequencing delays. These enhancements incorporate lessons from WhatsApp’s key transparency log operation over the past two years.
Key transparency is now active on Messenger, allowing users to automatically verify the authenticity of contacts’ encryption keys in one-on-one chats. This marks a further advancement in providing a secure and private service.


